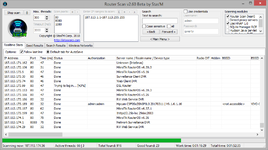
Router Scan is able to find and identify a variety of devices from large number of known routers and that the most important thing is to get from them useful information, in particular the characteristics of the wireless network: a method of protecting the access point (encryption), access point name (SSID) and access point key (passphrase).
Also it receives information about the WAN connection (useful when scanning a local network) and show the model of router.
Getting information occurs in two possible ways:
1. The program will try to guess a pair of username/password to the router from a list of standard passwords, thereby get access.
2. Or the vulnerabilities (bugs) will be used against the router model, allowing to get the necessary information and/or bypass the authorization process.
Wireless network detection and audit were added beginning with the version 2.60 including 802.11a/b/g/n standarts, you will need either an integrated or external Wi-Fi interface to use these functions.
3. WiFi service functions were also added to achieve best wireless audit results, WPA/WPA2 network key brute-force and WPS PIN audit along with Pixie Dust attack.
You must reply before you can see the hidden data contained here.

